Hard drives reportedly infected by NSA malware
Russian security software maker Kapersky Lab have found several hard drives with traces of a malware reportedly released by the NSA, named Fanny.
A report compiled recently by Russian security software maker Kapersky Lab indicates that the U.S. National Security Agency (NSA) has likely been infecting hard disk drives (HDDs) and solid-state drives (SSDs) for personal computers for almost two decades.
The report states that the specific malware, named Fanny, is linked to previous NSA spyware, such as the Stuxnet computer worm that sabotaged Iran’s nuclear program. Kapersky Lab does not directly state the NSA is involved, but rather puts the blame on the “Equation Group.”
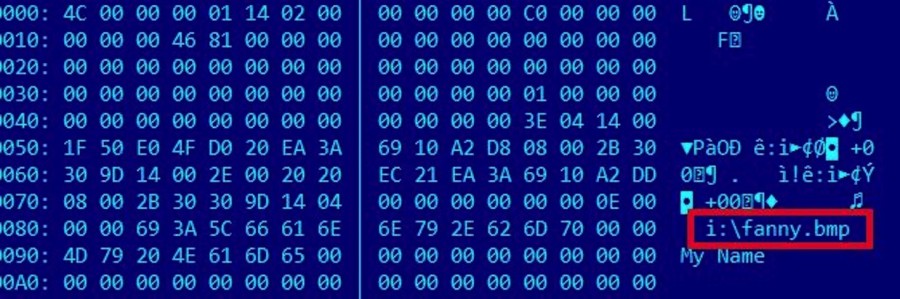
The malware targeting HDDs and SSDs, named Fanny, was created by the “Equation Group” and has been infecting computers for almost two decades.
According to principal security researcher at Kapersky Lab, Igor Soumenkov, there are no detection methods to check if a personal HDD is infected.
“There is no way to understand whether your HDD is infected. Once the hard drive gets infected with this malicious payload, it’s impossible to scan its firmware,” he said in an email reply to Computerworld. “It means that we are practically blind, and cannot detect hard drives that have been infected by this malware.”
The malware reportedly cannot be detected by antivirus programs either and can produce data for any government agency controlling the drive. Hard drive manufacturers Seagate, Western Digital, Toshiba, IBM, and Maxtor were affected, as well as SSD makers like Micron and Samsung.
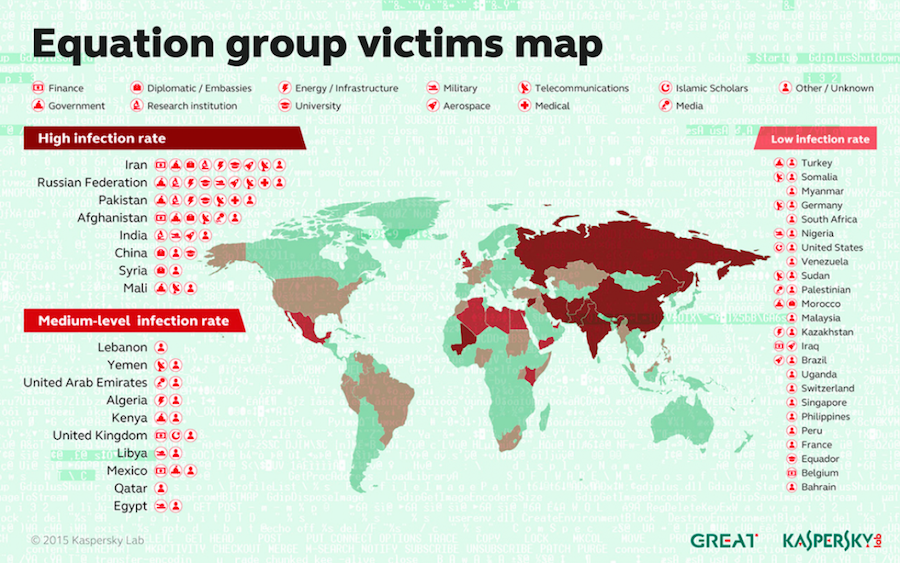
Some of the countries most impacted by Fanny include Iran, Russia, and Pakistan. The United States reportedly has a low infection rate.
According to Reuters, an employee confirmed that the NSA developed this specific technique but is unsure if they are responsible for using the malware.
Records indicate that while some malware samples were compiled in 2002, others were registered as early as 1996, nineteen years ago. During this time period, 30 countries were infected, with the most common including countries like Iran, Russia, and Pakistan.
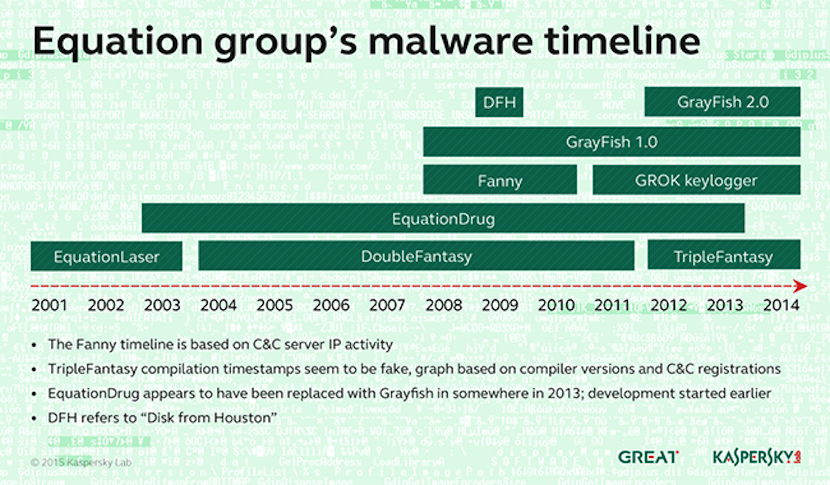
Although the Fanny timeline has been pinpointed from between 2008 to 2010, it may have been released as early as 1996.
The malware has mainly targeted government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists.
The full report of the malware released by Kapersky Lab can be found here.
Vineet Kosaraju (12) is the STEM Editor for both Harker Aquila and Winged Post. He is a senior and has been part of the journalism program for the past...


















![“[Building nerf blasters] became this outlet of creativity for me that hasn't been matched by anything else. The process [of] making a build complete to your desire is such a painstakingly difficult process, but I've had to learn from [the skills needed from] soldering to proper painting. There's so many different options for everything, if you think about it, it exists. The best part is [that] if it doesn't exist, you can build it yourself," Ishaan Parate said.](https://harkeraquila.com/wp-content/uploads/2022/08/DSC_8149-900x604.jpg)




![“When I came into high school, I was ready to be a follower. But DECA was a game changer for me. It helped me overcome my fear of public speaking, and it's played such a major role in who I've become today. To be able to successfully lead a chapter of 150 students, an officer team and be one of the upperclassmen I once really admired is something I'm [really] proud of,” Anvitha Tummala ('21) said.](https://harkeraquila.com/wp-content/uploads/2021/07/Screen-Shot-2021-07-25-at-9.50.05-AM-900x594.png)







![“I think getting up in the morning and having a sense of purpose [is exciting]. I think without a certain amount of drive, life is kind of obsolete and mundane, and I think having that every single day is what makes each day unique and kind of makes life exciting,” Neymika Jain (12) said.](https://harkeraquila.com/wp-content/uploads/2017/06/Screen-Shot-2017-06-03-at-4.54.16-PM.png)







![“My slogan is ‘slow feet, don’t eat, and I’m hungry.’ You need to run fast to get where you are–you aren't going to get those championships if you aren't fast,” Angel Cervantes (12) said. “I want to do well in school on my tests and in track and win championships for my team. I live by that, [and] I can do that anywhere: in the classroom or on the field.”](https://harkeraquila.com/wp-content/uploads/2018/06/DSC5146-900x601.jpg)
![“[Volleyball has] taught me how to fall correctly, and another thing it taught is that you don’t have to be the best at something to be good at it. If you just hit the ball in a smart way, then it still scores points and you’re good at it. You could be a background player and still make a much bigger impact on the team than you would think,” Anya Gert (’20) said.](https://harkeraquila.com/wp-content/uploads/2020/06/AnnaGert_JinTuan_HoHPhotoEdited-600x900.jpeg)

![“I'm not nearly there yet, but [my confidence has] definitely been getting better since I was pretty shy and timid coming into Harker my freshman year. I know that there's a lot of people that are really confident in what they do, and I really admire them. Everyone's so driven and that has really pushed me to kind of try to find my own place in high school and be more confident,” Alyssa Huang (’20) said.](https://harkeraquila.com/wp-content/uploads/2020/06/AlyssaHuang_EmilyChen_HoHPhoto-900x749.jpeg)



